Insider Tactics for Fraudulent Mobile App and ATM Deposits
In the hidden corners of the dark web, where anonymity rules and illicit activities occur on a daily basis, check fraudsters gather to share information. Dark web forums and marketplaces have become a fertile ground for information sharing, providing a space for criminals to exchange tips, techniques, and best practices. The following article draws upon several posts collected from the dark web to compile a “cookbook” created from the collective knowledge shared by people actively perpetrating check fraud.
Before we dive into the cookbook, it’s essential to understand the differences between the two primary check fraud methods used by these criminals:
Stolen/Altered Checks: Altered checks are genuine, stolen checks in which the information on the check has been changed to falsify the recipient, amount or account information. Some fraudsters use physical tools or chemicals (e.g, acetone, brake fluid) to erase information. Others may falsify information digitally.
Counterfeit Checks: Counterfeiting involves the creation of fraudulent checks that appear legitimate but are 100% fake. Fraudsters replicate bank logos, watermarks, and security features to deceive unaware victims and financial institutions. With advancements in printing/scanning technology, counterfeiters can produce high-quality fake checks that closely resemble authentic ones, making detection challenging.

Unfortunately, criminals now use sophisticated counterfeiting techniques where an original check is intercepted via mail theft—either by targeting an individual’s mailbox or attacking the supply chain (e.g., couriers, central mail processing centers). The check is then scanned and reprinted with a new beneficiary. Since the deposited item is a counterfeit check, the liability for identifying it as fraud falls on the originating bank. However, the high quality of these counterfeits makes detection extremely challenging.
The Check Fraud Cookbook
This “cookbook” is divided into two short, step-by-step guides, based on multiple posts collected from fraud forums: one for mobile check deposits and the other for physical check deposits at ATMs.

Visual 1. A stolen check (value: $1518.05) sold for $100 in a dark web marketplace. Source: Refine Intelligence/Daniel Shkedi.
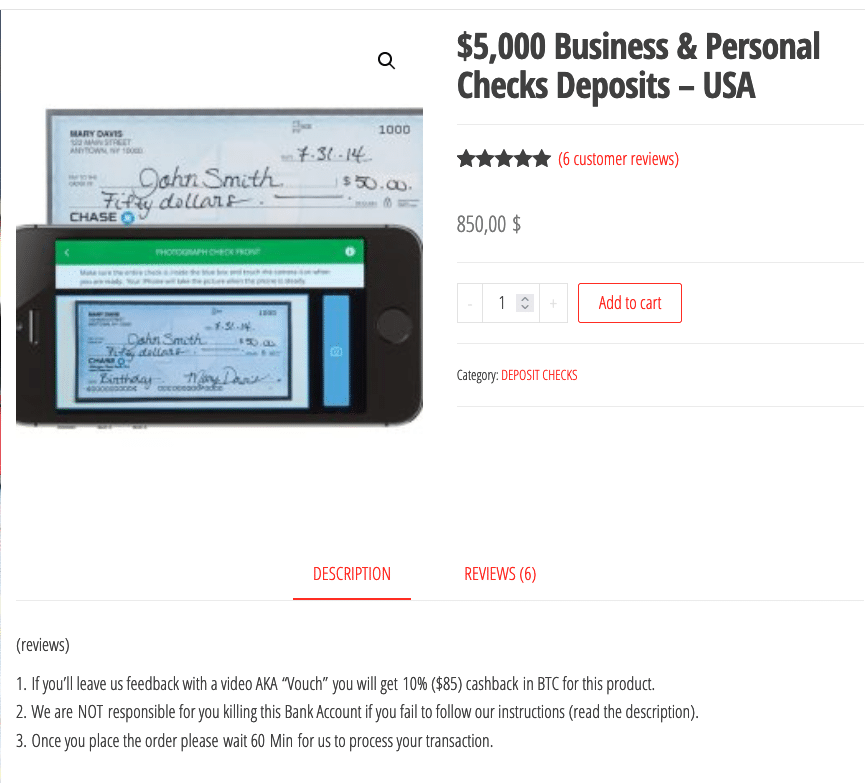
Visual 2. A check scan service offering scanned business and personal checks (value: $5000 per check) for $850. Source: Refine Intelligence/Daniel Shkedi.
I. Mobile Check Deposits
- Buy Check Scan: The first step in this fraud MO is acquiring a high-quality scan of a check. Fraudsters typically provide custom details to a service provider on the dark web and receive a clean scan in return. For those looking to be thorough, buying the stolen information along with the scan can provide an extra layer of deception.
- Print Scans: Surprisingly, the equipment needed for this step is nothing out of the ordinary. A regular printer and paper are enough to print high-quality checks that can pass most mobile check deposit systems.
- Choose Target: Selecting the right bank is crucial. Popular choices include banks with numerous branches across the U.S (top-10 banks).
- Choose Low Daily Limit: A critical step is reading and understanding the bank’s mobile deposit FAQ. This includes examining the endorsement policy, daily deposit limits, and cut-off times to avoid raising any red flags.
- OPSEC (Operational Security): Minimizing the digital footprint is extremely important. Fraudsters mask their IP addresses, format their phones after each deposit (back to factory settings), use VPNs or SOCKS5 proxies, and operate with burner phones and SIM cards to cover their tracks.
- Laundering: After successfully depositing the check, the next step in many cases is laundering the funds. This often involves using a debit card to make transactions at popular stores like CVS, Walmart, and Target. Buying gift cards and sending them to a mule is a common tactic.
- Bank Hold Release: If a bank holds the check the next day, the fraudster’s job isn’t done. They will call customer support (never the branch) and use an emergency story to convince the bank to release the hold manually.
- Quality Over Quantity: A recurring theme among fraudsters is that high-quality scans often yield better results. “The more you pay, the better quality you’ll get” is a mantra to live by in this line of work.
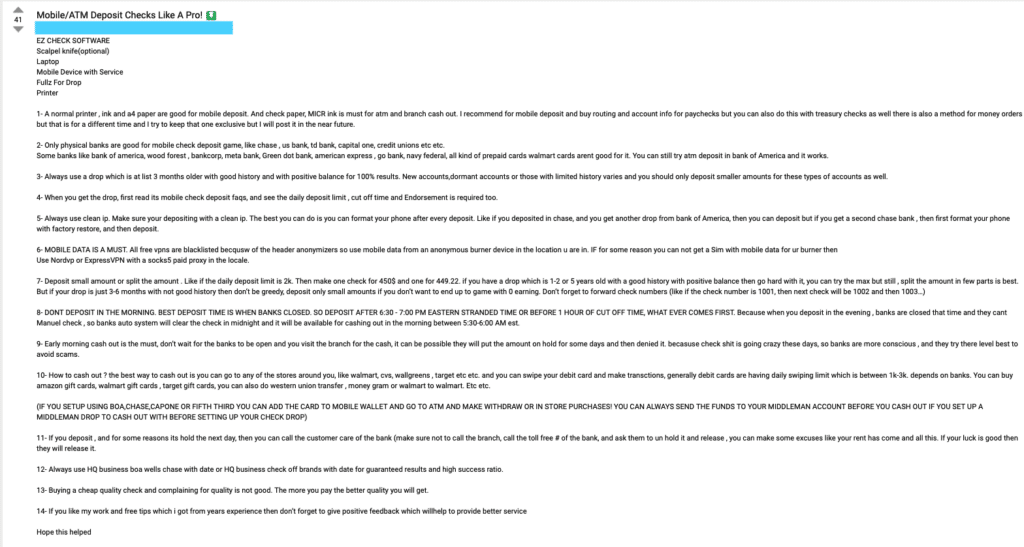
Visual 3. From the dark web: a check fraudster offering step-by-step, practical advice on how to deposit stolen checks at ATMs or on a mobile app. Source: Refine Intelligence/Daniel Shkedi.
II. Physical Check Deposits at ATMs
- Buy Physical Check: Just like with digital scans, the first step here is obtaining a physical check. These can be stolen (referred to as “glass” checks from different banks or U.S. Treasury checks) or forged, complete with high-quality MICR (Magnetic Ink Character Recognition) and security features.
- Set Up Bank Drop: The next step involves setting up a bank account, often referred to as a “drop.” Ideally, this account should be aged (over 90 days), have a good history, and maintain a positive balance.
- Small Amounts: Depositing small or split amounts is a strategy to avoid detection. Unless the drop account is well-aged, fraudsters typically deposit up to half the limit in installments.
- Deposit/Cash-Out Time: Timing is everything. Fraudsters will typically aim to deposit around 6:30-7 PM EST or one hour before the bank’s cut-off time to avoid manual reviews. Most systems auto-clear at midnight, making the best withdrawal time around 5:30-6 AM EST.
- Laundering: Similar to mobile deposits, funds are often laundered immediately after a successful deposit. This is often done through transactions at retail stores and buying gift cards, which are then sent to a mule for further laundering.
- Bank Hold Release: If the bank places a hold on the check, the fraudster will contact customer support with an emergency story to have the hold released manually.
- Disguise: Physical deposits require extra caution. Surveillance cameras are everywhere around the branch/ATM, so fraudsters often wear COVID masks, gloves and park their cars across the street to avoid detection.
- Quality Over Quantity: Just as with digital check scams, investing in higher quality checks and equipment pays off. “The more you pay, the better quality you’ll get” holds true here as well.

Visual 4. A lively conversation in a fraud forum on the dark web about precautions before physical check deposits at ATMs. Source: Refine Intelligence/Daniel Shkedi.
Into the Mind of a Check Fraudster
Going into the minds of check fraudsters and analyzing dark web intelligence is crucial in combating the growing sophistication of check fraud. As these criminals continue to refine their techniques and share their knowledge, the threat to the U.S. banking sector increases. By understanding their methods and how they actually deposit checks, bank fraud teams and other departments can try to stay one step ahead in this ongoing battle against this rampant type of financial crime.
Learn how Refine helps banks prevent check fraud with Digital Customer Outreach.